Discovering API Authentication
I never realized how crucial APIs are until I delved into the world of securing them, where verifying identities can mean the difference between safe data access and potential breaches that threaten entire systems.
This exploration uncovers the essentials of API authentication, revealing methods that protect sensitive information while hinting at the fine line between access and control.
TL;DR
I learned that API authentication verifies client identities, much like checking an ID at a secure entrance, to prevent unauthorized access and data risks.
It enhances security by tracking usage and applying limits, ensuring only verified users interact with APIs without overwhelming the system.
From simple HTTP Basic Auth to advanced JWT and OAuth 2.0, each method offers unique benefits but requires careful implementation for safety.
Authentication focuses on "who you are," while authorization determines "what you can do," clarifying a key distinction that strengthens overall API protection.
Mastering these techniques reveals scalable solutions for modern apps, sparking curiosity about evolving security challenges ahead.

APIs form the backbone of today's applications, enabling systems to communicate seamlessly, but I quickly understood that we must verify who is accessing them to avoid risks.
In my journey, API authentication emerged as the key process for confirming a client's or user's identity, similar to checking identification before entering a restricted area.
This verification ensures that only authorized entities can reach sensitive data, preventing scenarios where anyone with the API URL could exploit it, leading to breaches or misuse.
The main reason I emphasize API authentication is for enhanced security; it restricts access to verified clients, minimizing threats like attacks or unauthorized data exposure.
By identifying users, providers can tailor permissions, track interactions for auditing, and even enforce rate limits to handle traffic without overload.
This approach not only bolsters protection but also helps in analyzing usage patterns, giving a clearer picture of how APIs are utilized in real-world scenarios.
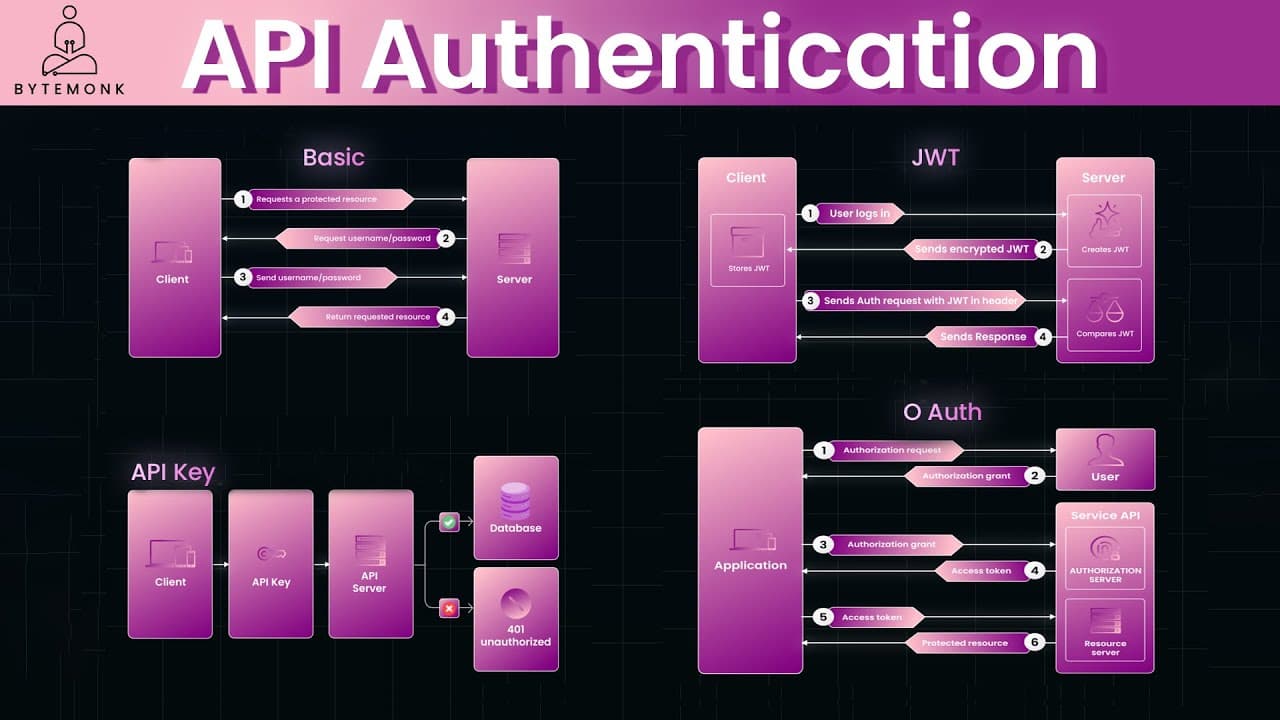
When I explored the common methods, I started with HTTP Basic Authentication, where credentials like a username and password are sent in the HTTP header, encoded in Base64 for identification.
Though straightforward, I noted its vulnerabilities, as these credentials travel with every request and can be intercepted unless paired with HTTPS for encryption.
Next, API key authentication involves issuing a unique key to clients, which they include in requests to identify themselves, allowing providers to monitor and control usage effectively.
However, if a key is compromised, revoking access becomes tricky, so I always recommend using HTTPS to protect transmission and limit exposure.
Moving on, JSON Web Tokens (JWT) stood out as a compact, stateless option; after a user logs in, the server generates a signed and encrypted token containing their identity.
This token is then sent with subsequent requests, where the server validates it without needing to store session data, making it ideal for scalable environments.
I found JWT appealing because it prevents tampering and supports efficient authentication, though it requires secure handling to maintain integrity.
Finally, OAuth 2.0 impressed me as the modern standard, enabling users to authenticate via trusted services like Google without sharing direct credentials.
It uses access tokens that can expire or be revoked, offering granular control and better scalability than older versions, making it a go-to for secure API integrations.
One confusion I cleared up was the difference between authentication and authorization; authentication simply confirms "who you are" by verifying identity.
Authorization, on the other hand, decides "what you can do" by checking permissions after authentication, like allowing a regular user to view data while restricting admins to edits.
This distinction is vital, as it ensures that even after verifying identity, access remains controlled and appropriate.
In my experience, combining these elements creates a robust system where APIs are both secure and functional.
Reflecting on this, API authentication has proven to be a foundational step in building trustworthy digital connections, highlighting how simple verifications can safeguard complex ecosystems.
As technology evolves, these methods will continue to adapt, paving the way for even more secure and efficient interactions in the future.
Key Takeaways
API authentication verifies client identities to prevent unauthorized access and enhance security.
Common methods include HTTP Basic Auth, API keys, JWT for stateless verification, and OAuth 2.0 for scalable control.
It differs from authorization by focusing on identity rather than permissions, forming a complete access strategy.